Recovery Service Vault In Same Resource Group?
Last Updated on October vi, 2019 past
In my terminal few blog posts, I take explained how we can encrypt Azure VMs (Windows & Linux) using BitLocker & dm-crypt. You tin can access these manufactures using the following links,
Step-by-Pace Guide to Encrypt Azure Windows VM using BitLocker (PowerShell Guide) – https://www.rebeladmin.com/2019/09/pace-pace-guide-encrypt-azure-windows-vm-using-bitlocker-powershell-guide/https://world wide web.rebeladmin.com/2019/09/pace-pace-guide-encrypt-azure-windows-vm-using-bitlocker-powershell-guide/
Step-by-Step Guide to Encrypt Azure Linux VM (PowerShell Guide) – https://www.rebeladmin.com/2019/09/footstep-stride-guide-encrypt-azure-linux-vm-powershell-guide/
When we encrypt consummate disks, it not only encrypting the files in there. It also encrypts file system data which uses past the operating organisation. The operating system itself doesn't have an issue accessing content as it is aware of the key information. But any other organisation can't access this content without the encryption central information. This is the same when it comes to backup and restore. In this demo, I am going to demonstrate how we can fill-in and restore an encrypted Azure VM using Azure Fill-in.
Equally with whatsoever other backup solution, Azure fill-in also has a certain limitation when it comes to encrypted data fill-in/restore.
1. Encrypted VM backup/restore only supported inside the same region & same subscription.
2. Azure backup simply supports the VM which is encrypted using standalone keys.
three. When information technology comes to data restore, Encrypted VM required full restore. It can't recover data in files or folders level.
4. When restoring VM, Azure backup tin't utilize supercede existing VM choice for encrypted VMs.
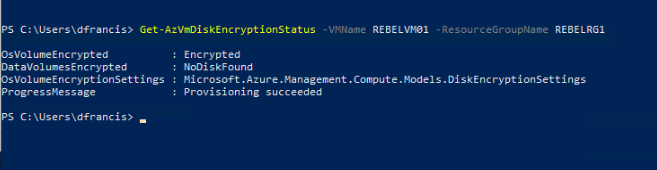
In my demo surroundings, I already have an encrypted windows VM called REBELVM01. I am going to back up information technology and restore using Azure Backup.
Create a Recovery Services backup vault
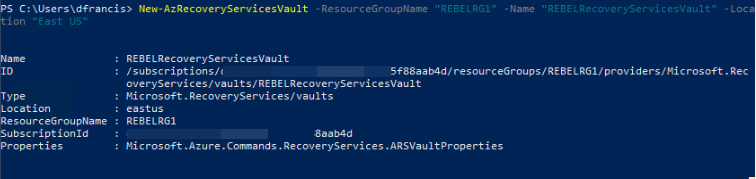
Before we get alee with fill-in, start we need a recovery service backup vault. Information technology can exist created using,
New-AzRecoveryServicesVault -ResourceGroupName "REBELRG1" -Name "REBELRecoveryServicesVault" -Location "East Usa"
[su_note]I am using Azure PowerShell module here. Y'all can find more than info virtually information technology under https://docs.microsoft.com/en-us/powershell/azure/install-az-ps?view=azps-2.6.0[/su_note]
In the above, I am creating a recovery service vault called "REBELRecoveryServicesVault" in the aforementioned resource grouping as my encrypted VM.
Grant Permissions
To fill-in encrypted VMs, Azure backup service required read-only admission to encryption keys & secrets. To grant required permissions,
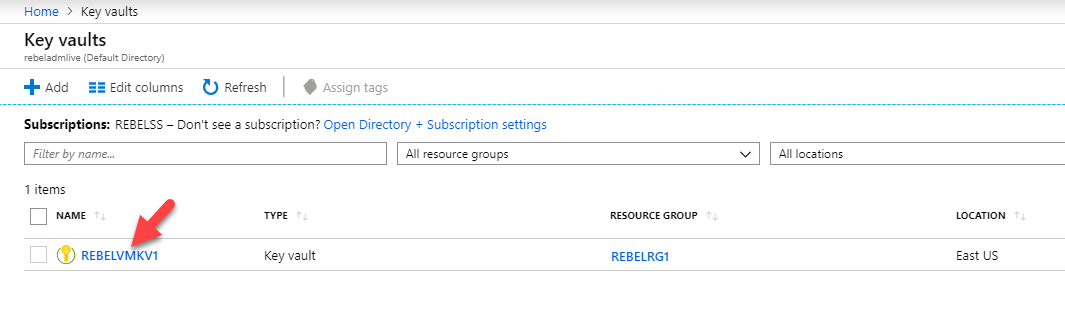
1. Log in to Azure portal every bit global administrator (https://portal.azure.com)
2. Go to All services | Cardinal vault
three. And so click on the relevant key vault
4. In the new window, click on Access Policies | Add Access Policy
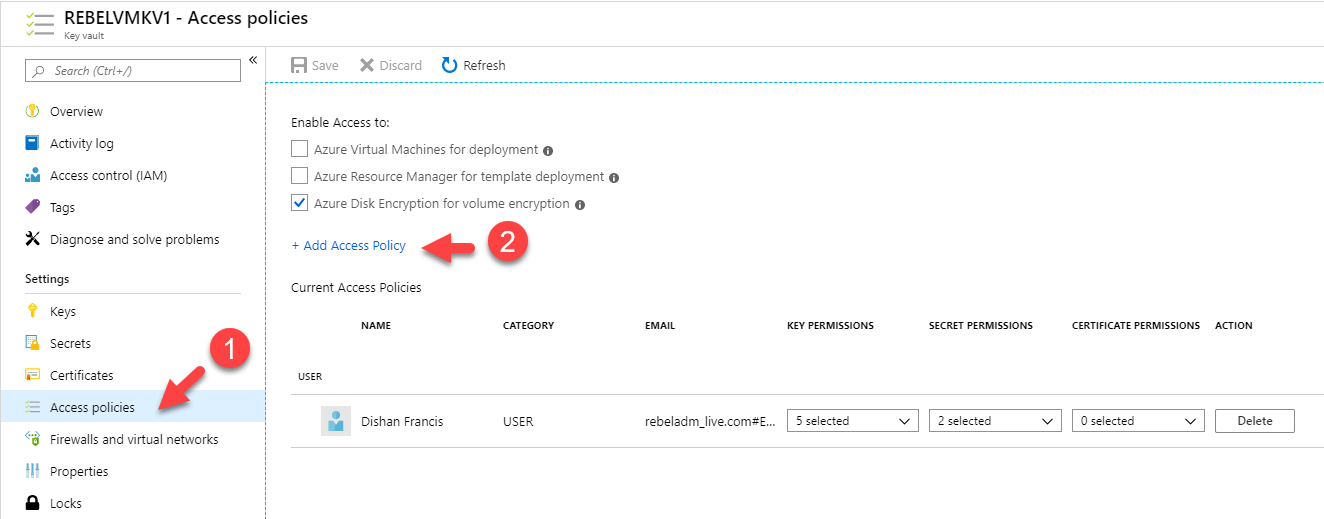
5. So click on Configure from a template (optional) drop-down and select Azure Backup
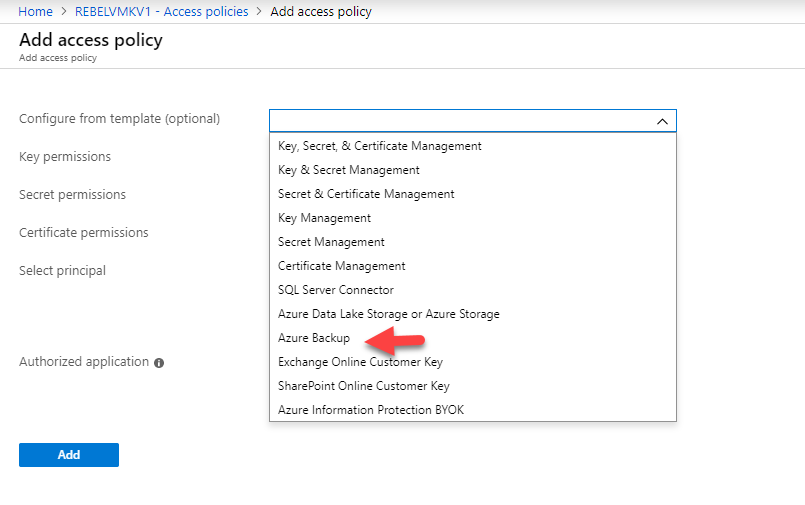
half-dozen. Once the selection is done, click on Add.
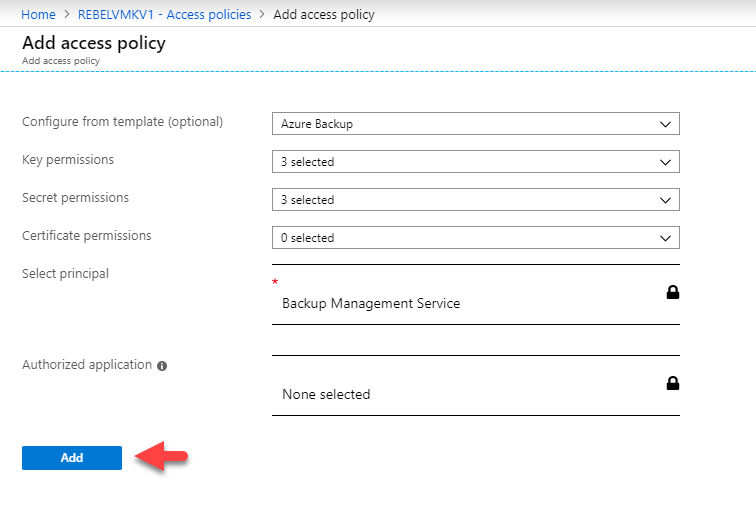
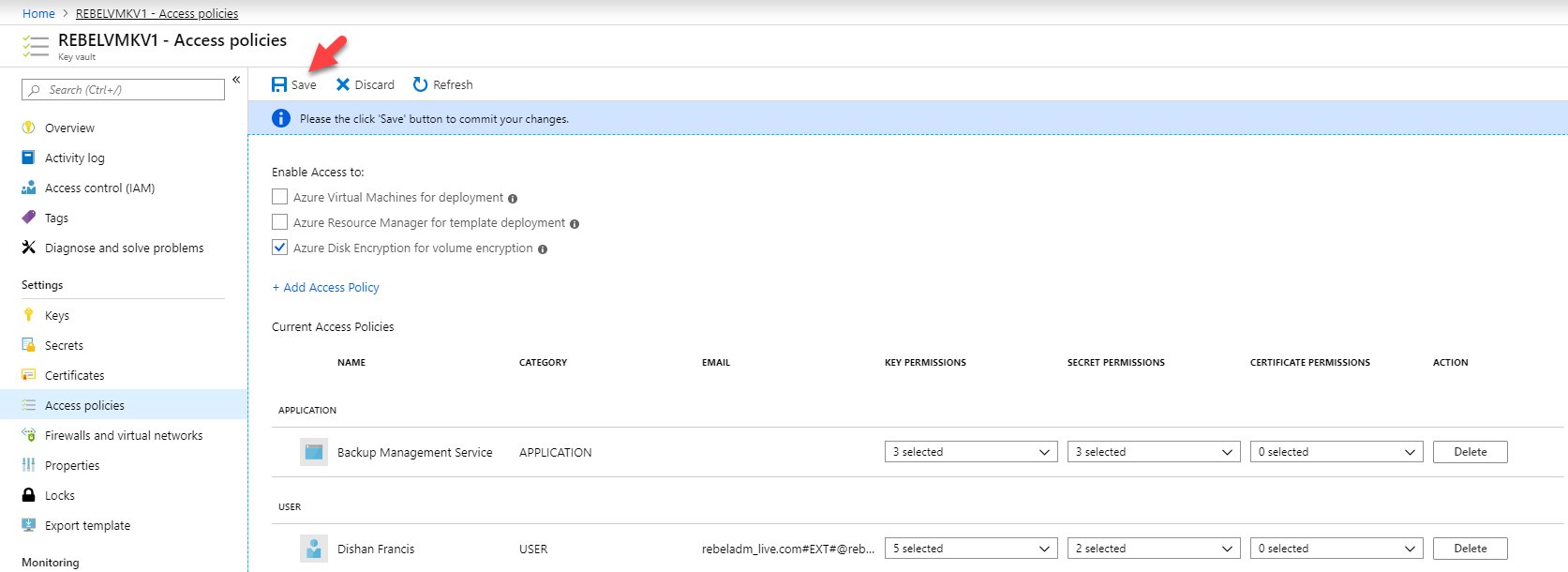
7. In the policy window, click on Relieve to apply the policy.
Create Backup policy
As the side by side step, I am going to create a new fill-in policy. The backup policy defines when the backup will run and how long information technology will keep data in the vault. To practice this,
1. Log in to Azure portal as global administrator (https://portal.azure.com)
2. Go to All services | Recovery Services vaults
3. And then click on the fill-in vault we created in one of the previous steps.
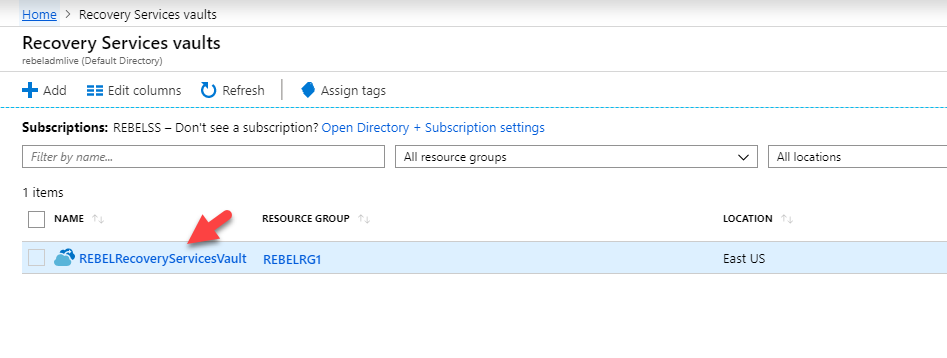
4. In the new window click on Backup policies | + Add
5. It will open upwards a new wizard. Select Azure Virtual Machine as the policy type.
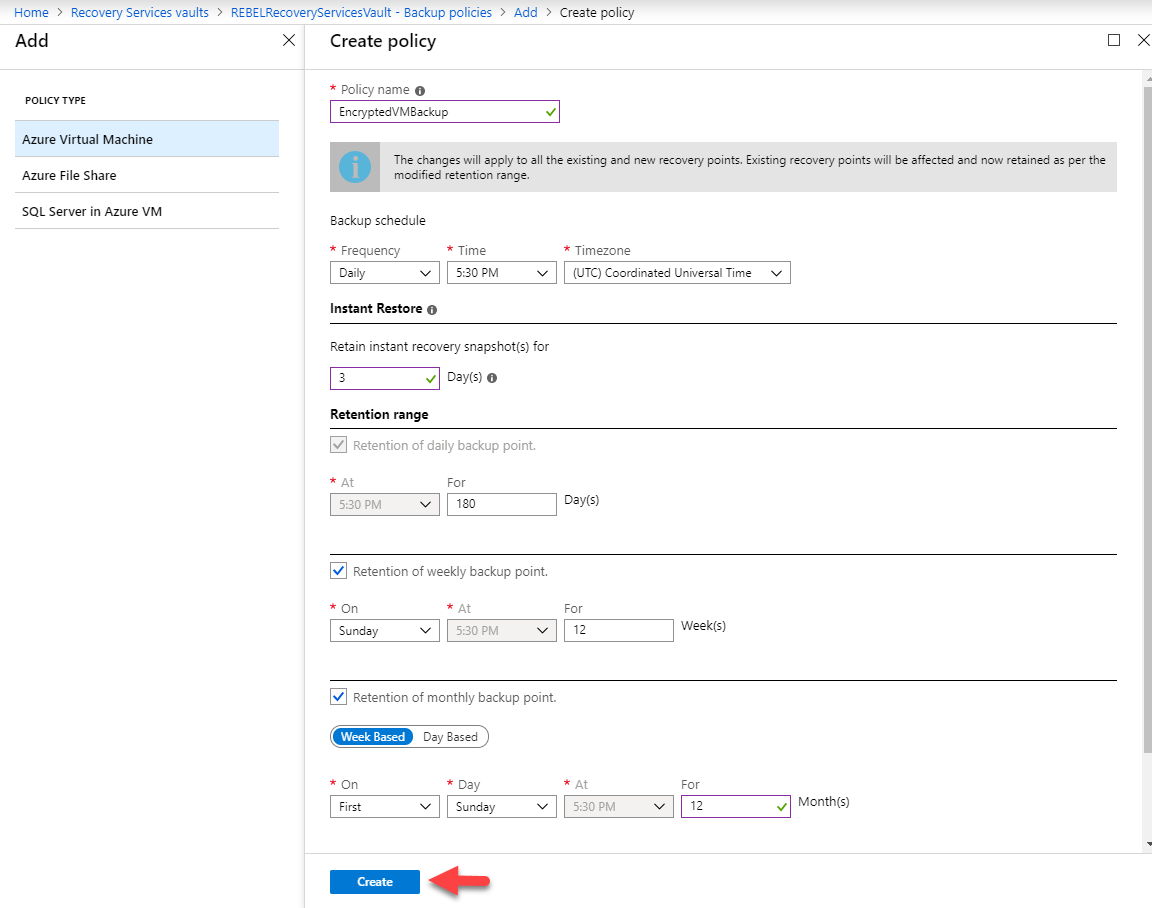
half-dozen. Then ascertain policy name and policy settings according to your requirements. In my demo,
• Policy name: EncryptedVMBackup
• Frequency: Daily v:thirty PM (UTC)
• Retain instant recovery snapshot(s) for: 3
• Daily backup betoken retention: 180 days
• Weekly backup indicate retention: Sunday for 12 weeks
• Monthly backup point retention: First Sunday for 12 months
Once policy settings are divers, click on Create.
Configure a fill-in for Encrypted VM
The adjacent step of the configuration is to adhere the newly created policy to Encrypted VM.
We tin do this using the following PowerShell commands,
Get-AzRecoveryServicesVault -Name "REBELRecoveryServicesVault" | Set-AzRecoveryServicesVaultContext
In the above command, I am setting the recovery vault context to the new service vault we created.
$a = Get-AzRecoveryServicesBackupProtectionPolicy -Name "EncryptedVMBackup"
Enable-AzRecoveryServicesBackupProtection -ResourceGroupName "REBELRG1" -Proper noun "REBELVM01" -Policy $a
In the to a higher place commands, I am enabling backup for REBELVM01 and attaching the EncryptedVMBackup policy.
Testing Recovery
For testing purposes, you practise not have to wait until the task kicks off. You still can go to backup items in the service vault and force the backup to run.
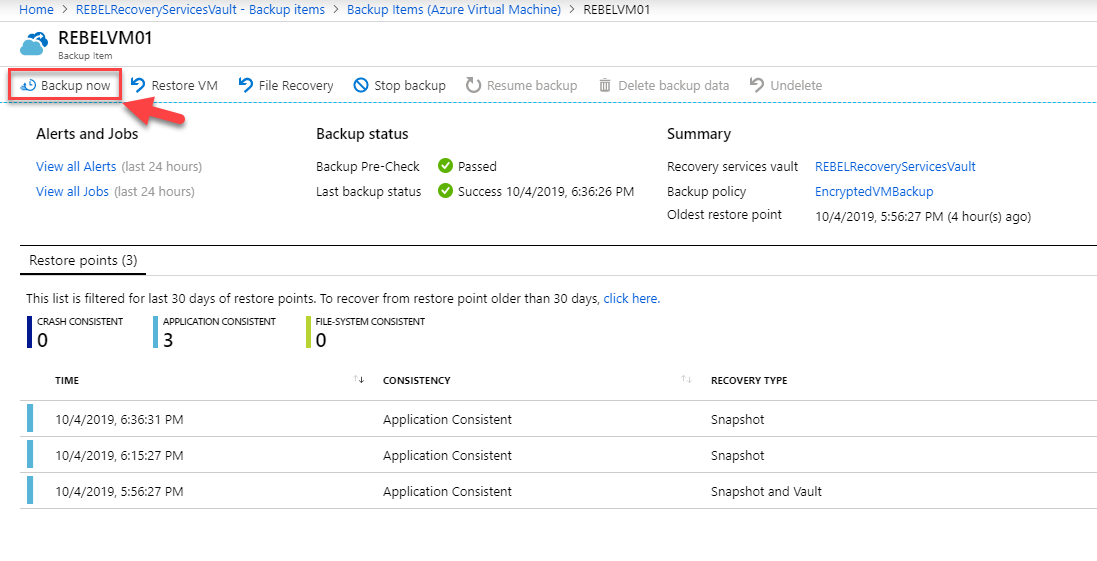
We can verify the status of the backup using,
Go-AzRecoveryservicesBackupJob
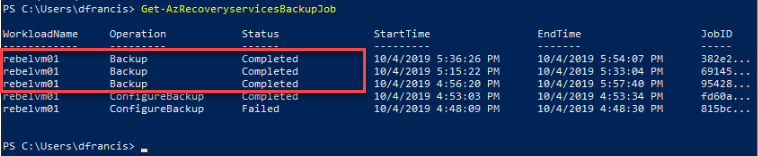
For testing purposes, I am going to end the encrypted VM and try to restore it.

To restore the VM, we need to go to All Services | Recovery Service Vaults | REBELRecoveryServicesVault (this is the service vault used in the demo)
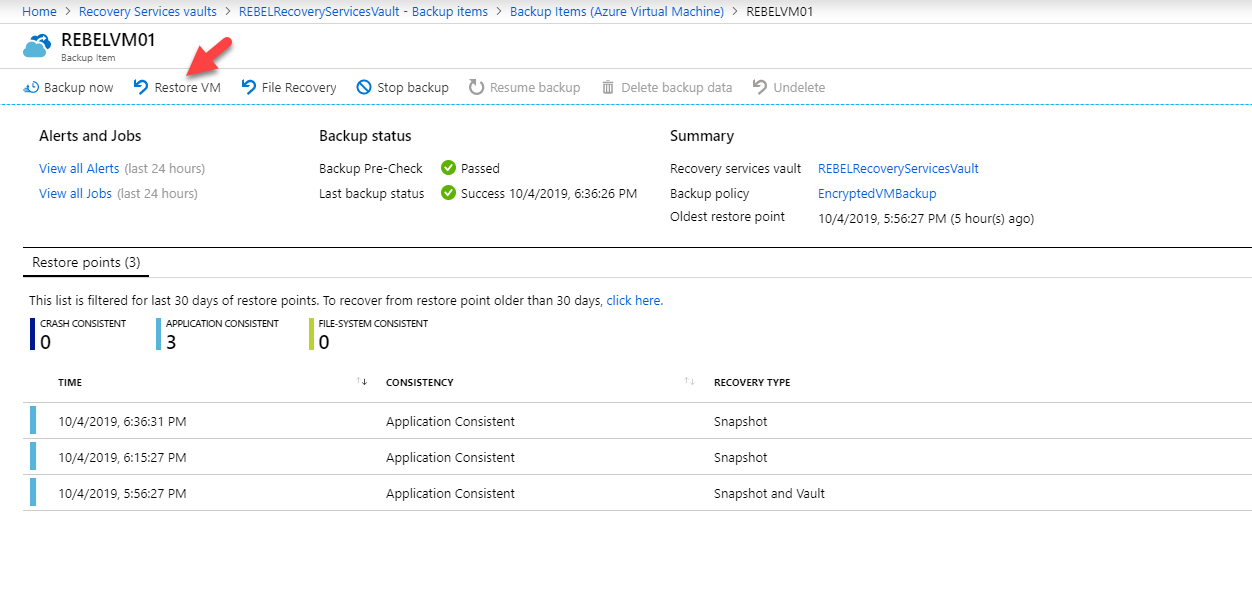
Then Fill-in items | Azure Virtual Auto then click on the REBELVM01
To restore VM disks, click on the Restore VM option.
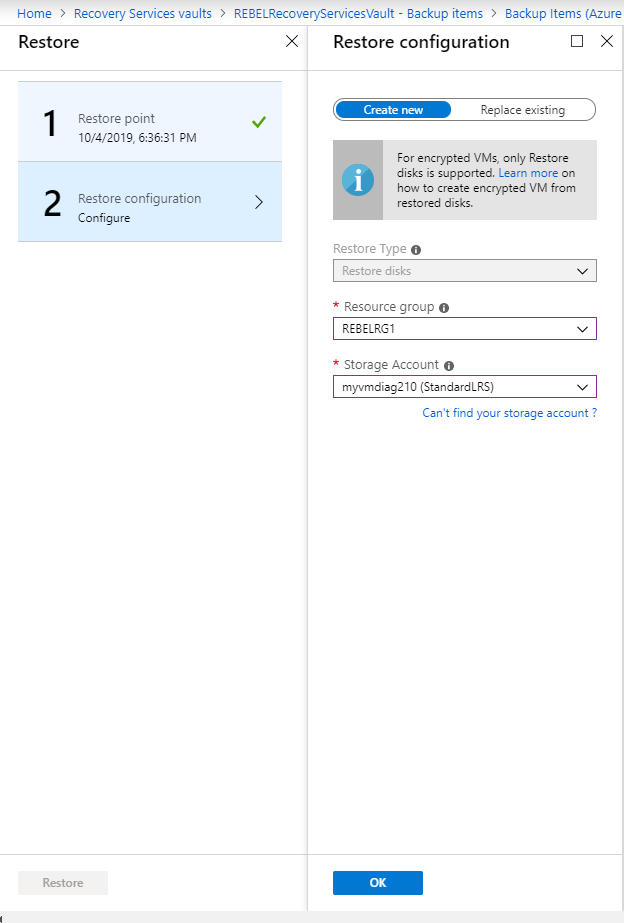
Then in the new wizard, select the fill-in y'all wish to restore and then select the aforementioned resource group and storage business relationship that VM was using. Delight remember yous can't utilize replace existing VM option with encrypted VM.
This restore job will only restore the disks. We need to create a VM using it.
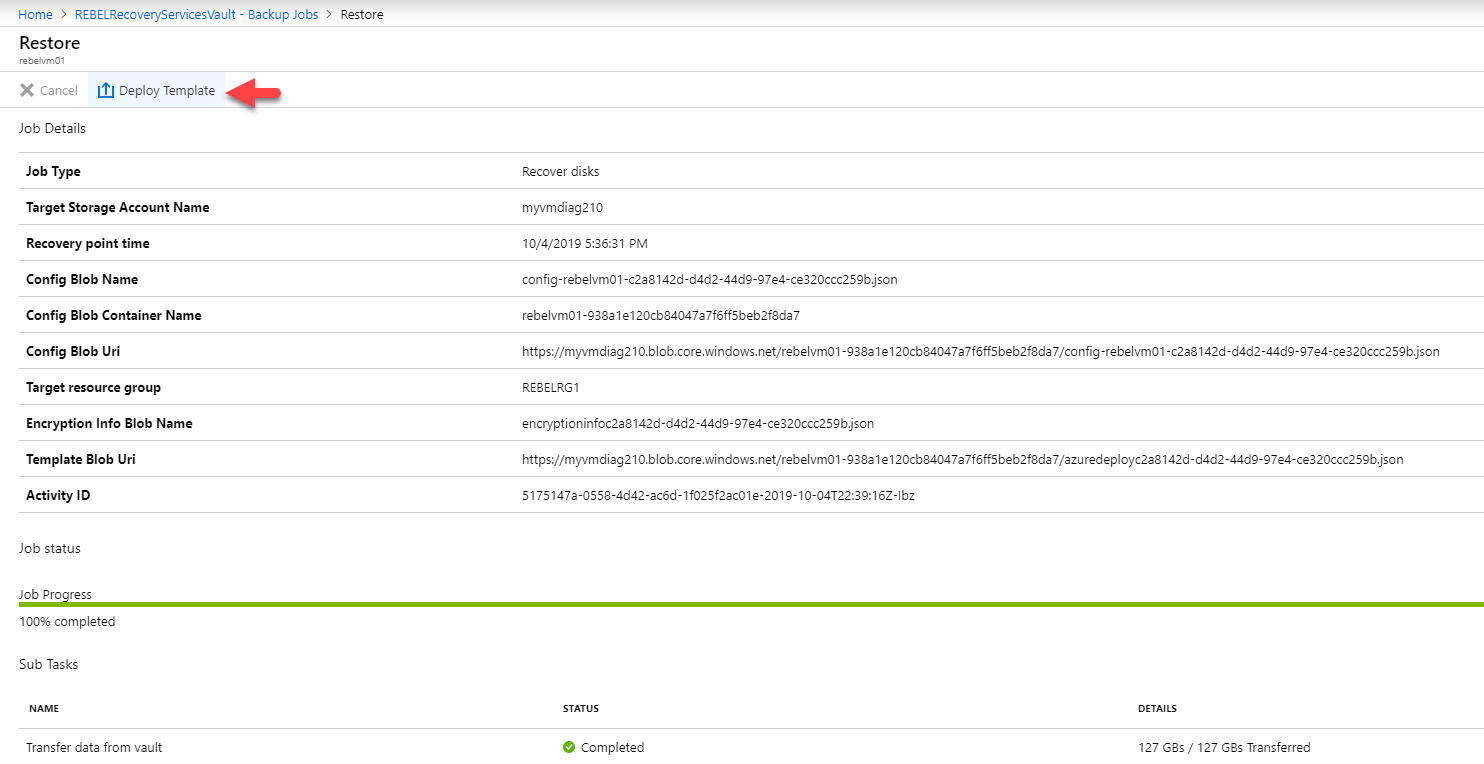
To exercise that go to Backup Jobs and click on the completed restore job.
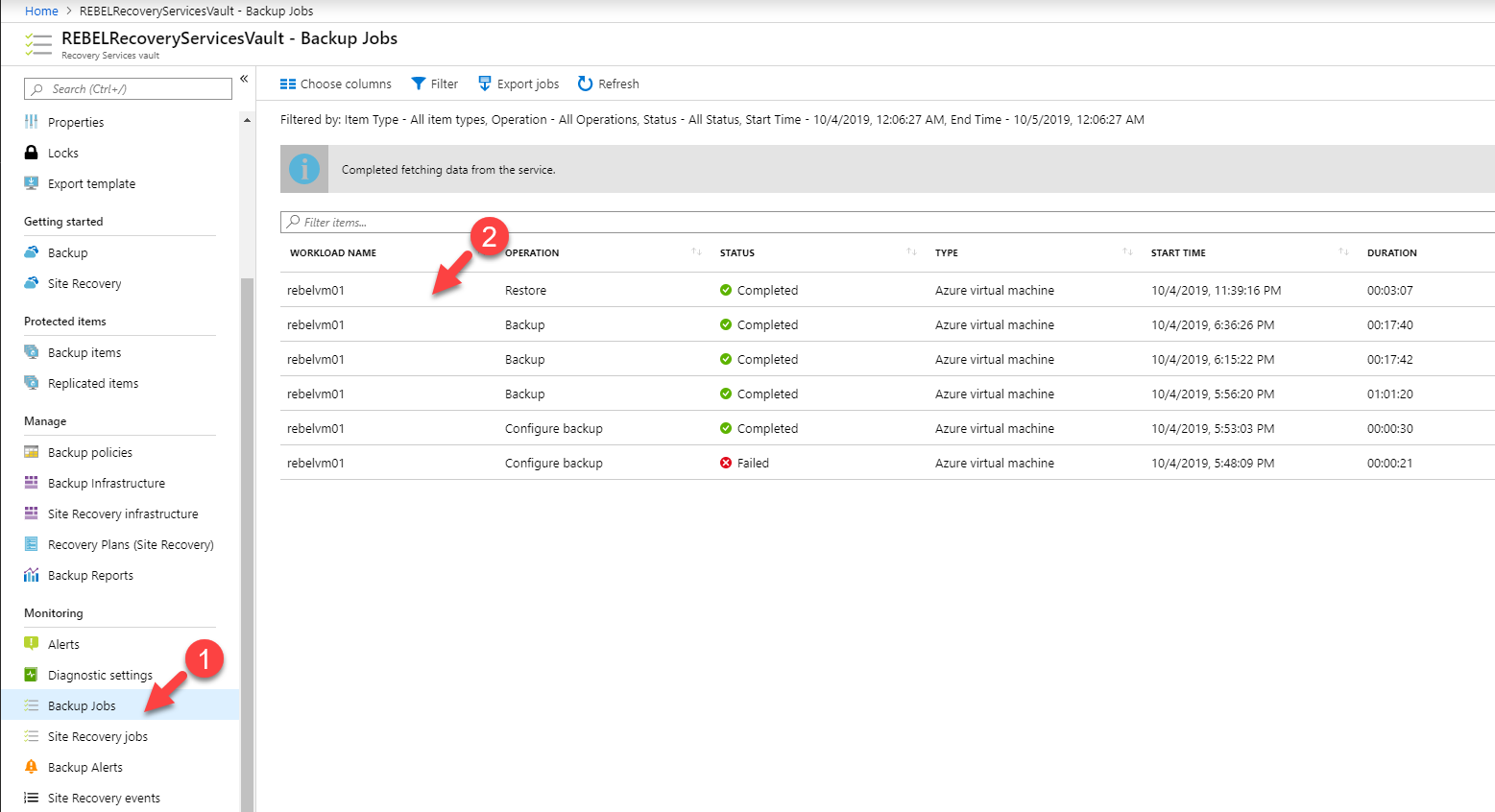
Then click on the Deploy Template option.
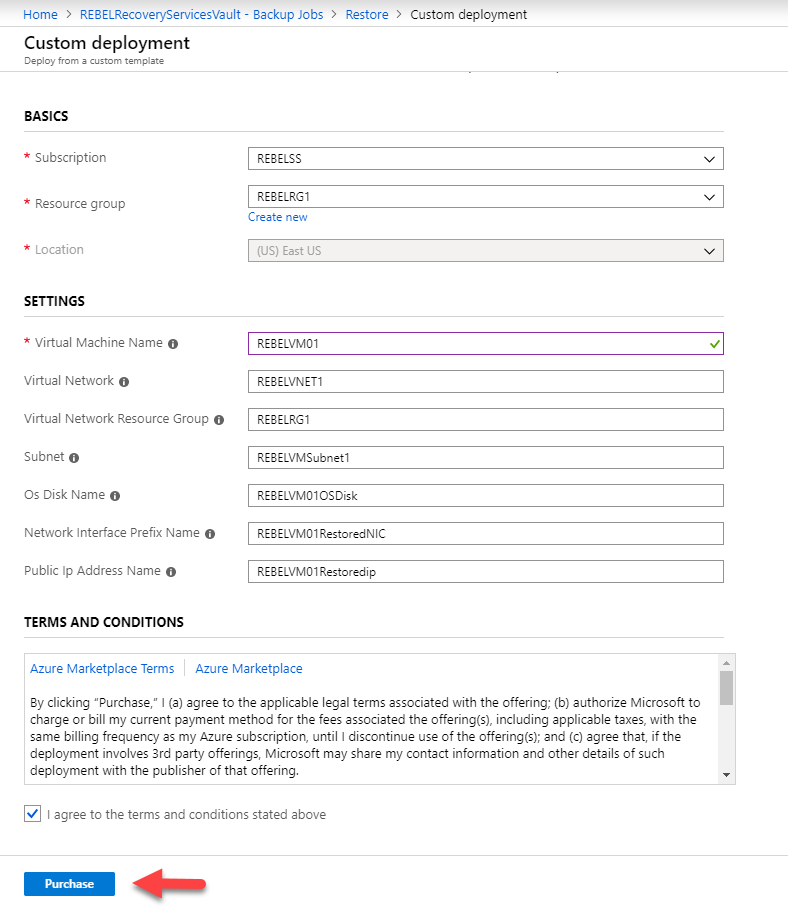
In new wizards, fill the relevant info (resource group, region & VM name) then click on Purchase.
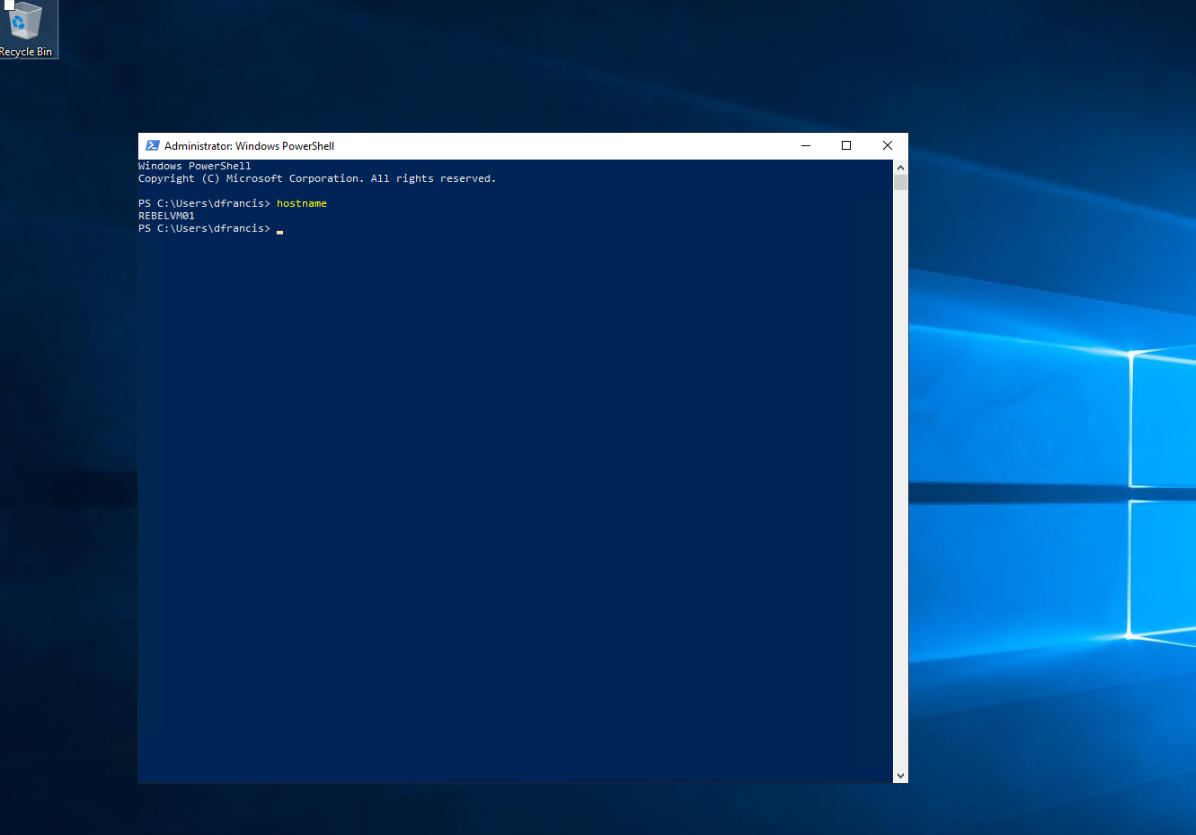
After the restore process completed, I can access the encrypted VM successfully.
And it is continued to be an encrypted VM.
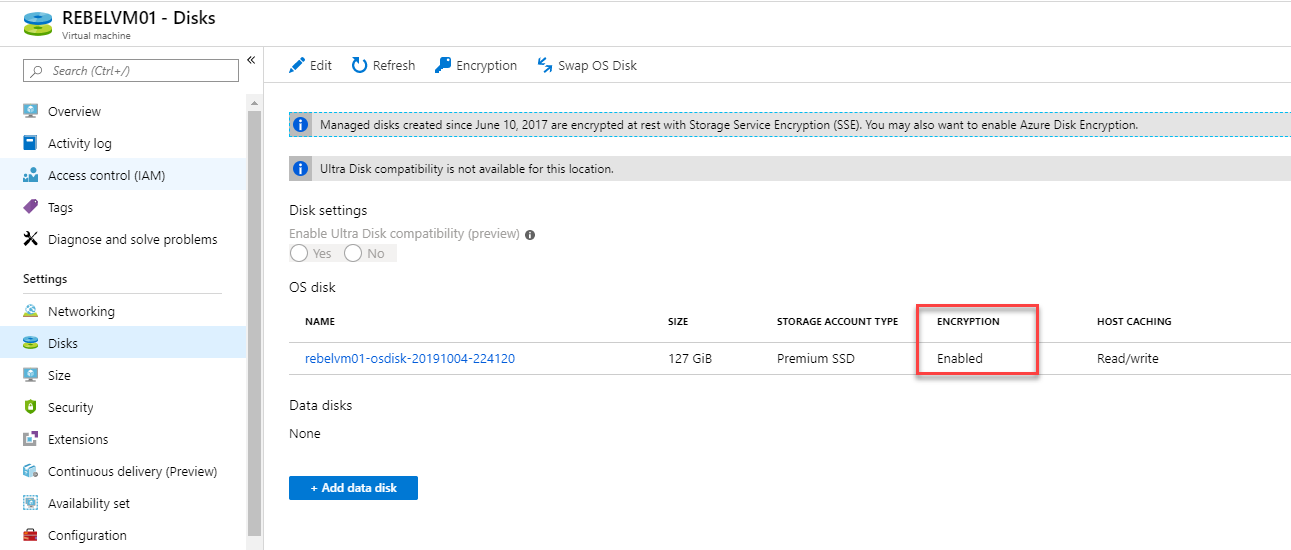
As we tin can see the backup and restore procedure of encrypted Azure VM is working as expected. This marks the end of this weblog postal service. If yous accept whatever further questions feel free to contact me on rebeladm@alive.com also follow me on twitter @rebeladm to get updates about new blog posts.
Recovery Service Vault In Same Resource Group?,
Source: https://www.rebeladmin.com/2019/10/step-step-guide-backup-restore-encrypted-azure-vm-using-azure-backup/
Posted by: walkerthlent.blogspot.com


0 Response to "Recovery Service Vault In Same Resource Group?"
Post a Comment